Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');]
Negative robots can be set up on end-user gadgets endangered by assailants, developing massive botnets. These tools could be residence computers, servers, as well as Io, T devices such as video game consoles or smart Televisions.
8 Easy Facts About Cyber Security Company Explained
Credibility monitoring likewise enables you to strain unwanted website traffic based upon resources, locations, patterns, or IP blacklists. File safety is vital to make sure sensitive data has not been accessed or damaged by unapproved parties, whether inner or external. Lots of conformity criteria require that organizations put in location rigorous control over delicate information files, show that those controls remain in location, and also show an audit trail of documents task in situation of a breach.
Discover concerning electronic possession monitoring (DAM), a business application that shops abundant media, as well as just how to take care of and protect it.
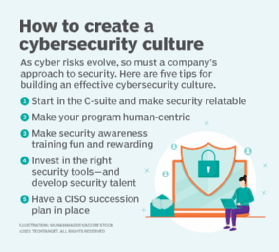
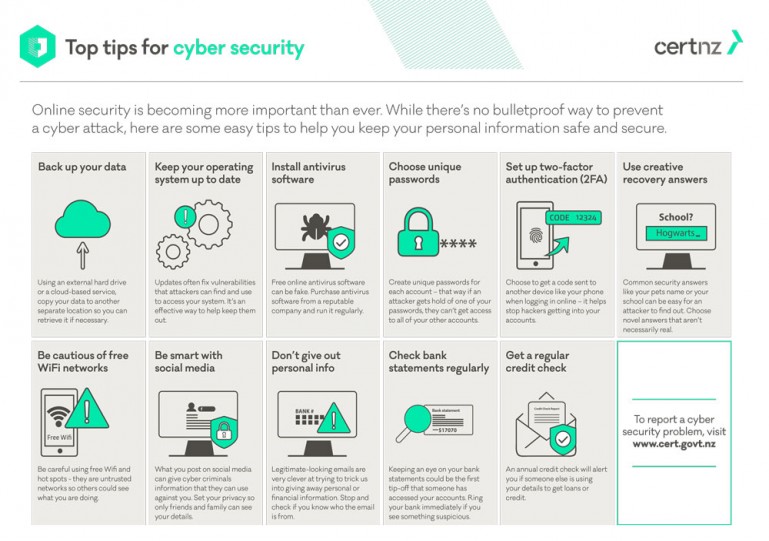
Keeping cybersecurity while functioning from house is challenging yet important. Do you have a growth group that works from another location? It can be frightening to believe concerning all the personal information that is left vulnerable via dispersed teams. Security finest techniques are not tricks. You just have to understand where to find the information.
Some Ideas on Cyber Security Company You Need To Know
Known as try this details innovation (IT) safety and security or digital information safety and security, cybersecurity is as much about those that utilize computer systems as it is regarding the computers themselves. Poor cybersecurity can put your individual information at risk, the risks are simply as high for companies and government divisions that deal with cyber risks.
As well as,. And it do without stating that cybercriminals that access the secret information of federal blog here government establishments can almost single-handedly interfere with business customarily on a wide range for better or for even worse. In recap, disregarding the value of you can try this out cybersecurity can have a negative impact socially, financially, and also also politically.
Within these three major classifications, there are numerous technological descriptors for exactly how a cyber hazard runs. Also within this details group, there are different parts of malware including: a self-replicating program that infects tidy code with its replicants, customizing various other programs malicious code camouflaged as legit software program software that intends to collect info from a person or organization for destructive purposes software application made to blackmail individuals by securing essential data software that automatically displays undesirable advertisements on a customer's user interface a network of connected computers that can send spam, take information, or concession personal information, among various other points It is one of the most typical web hacking assaults as well as can harm your data source.